Verifying installers
How to verify installer signatures?
Oct 31, 2019 at 12:25 Adrian
In order to verify that the ZSVPN client files have not been corrupted during download or tampered with, hash functions such as MD5 and/or SHA3 can be used. These one-way cryptographic algorithms produce a unique string that can be calculated from the downloaded file and compared to that listed on the Downloads page.
If the strings match, it is safe to assume that the binary/archive downloaded is a bit matched copy of that on our server.
To generate your own MD5/SHA3 hash from a downloaded file, follow the steps below.
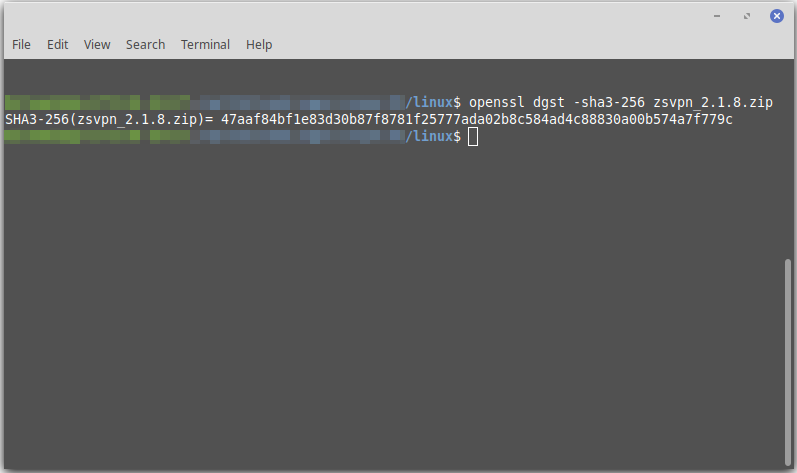
Linux
Step [1] - Install OpenSSL OpenSSL may already be installed depending on your distribution. Use "apt get install openssl" in Debian-based or "yum install openssl" for Red Hat-based.
Step [2] Run "openssl dgst -md5 zsvpn.zip" or "openssl dgst -sha3-256 zsvpn.zip"
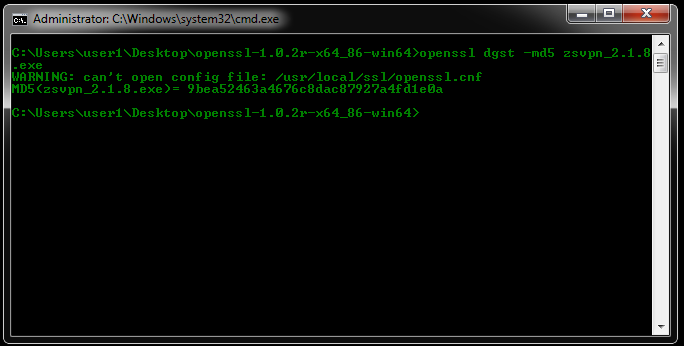
Windows
Step [1] - OpenSSL Click here to see a list of binaries endorsed by openss.org.
Our recommendation is Indy. Download a binary compatible with your machine. For example, openssl-1.0.2r-x64_86-win64.zip.
Step [2] Extract the contents of the archive to a folder and open a command prompt with Shift+Right-Click.
Step [3] Run "openssl dgst -md5 zsvpn.exe" or "openssl dgst -sha3-256 zsvpn.exe"
OS X
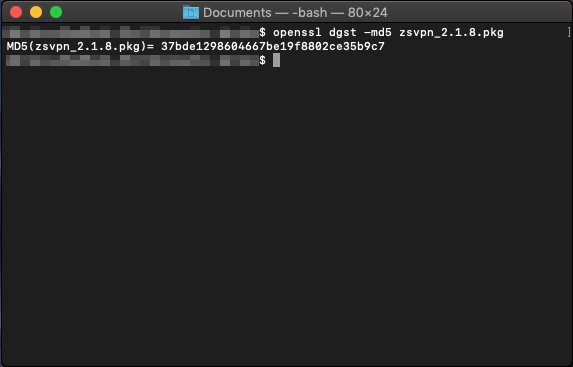
Step [1] - OpenSSL OpenSSL is already installed on recent version of OS X
Step [2] Run "openssl dgst -md5 zsvpn.pkg" or "openssl dgst -sha3-256 zsvpn.pkg"